Hackers solve problems and build things, and they believe in freedom and voluntary mutual help. To be accepted as a hacker, you have to behave as though you have this kind of attitude yourself. And to behave as though you have the attitude, you have to really believe the attitude.
Source:
<body onLoad=password()>
{
var a=”null”;
function check()
{
if (document.a.c.value == a)
{
document.location.href=”http://www.hackertest.net/”+document.a.c.value+”.htm”;
}
else
{
alert (“Try again”);
}
}
}
From the source code we can tell function check() checks to see whether the user input is equal to a. In the first line the code tells us var a = “null” so that should be the correct password.
Level 2For this level the password is again included in the source code:
Level 3var pass, i;
pass=prompt(“Please enter password!”,””);
if (pass==”l3l“) {
window.location.href=”http://www.hackertest.net/”+pass+”.htm”;
i=4;
}
Source:
Level 4 and 5<body onload=javascript:pass(); alink=”#000000″>
function pass()
{
var pw, Eingabe;
pw=window.document.alinkColor; // pw=#000000
Eingabe=prompt (“Please enter password”);
if (Eingabe==pw) // if prompt for password = #000000
{
window.location.href=String.fromCharCode(97,98,114,97,101)+”.htm”;
}
else
{
alert(“Try again”);
}
}
I had to google the answer to this one. The password is SAvE-as hELpS a lOt. I have no idea how people were able to get the source code on this one because it just kept taking me back to the previous level. Moving along.
Level 6Source:
<!–
var pass, i;
//–>
</script>
< h1>Hacker Test</h1>
<p>Test your hacking skills</p>
<br><br>
<h1>Level 6</h1>http://strongpsswd.js/strong
<br><br>
<center><p>Try again …</p></center>
Click passwd.js
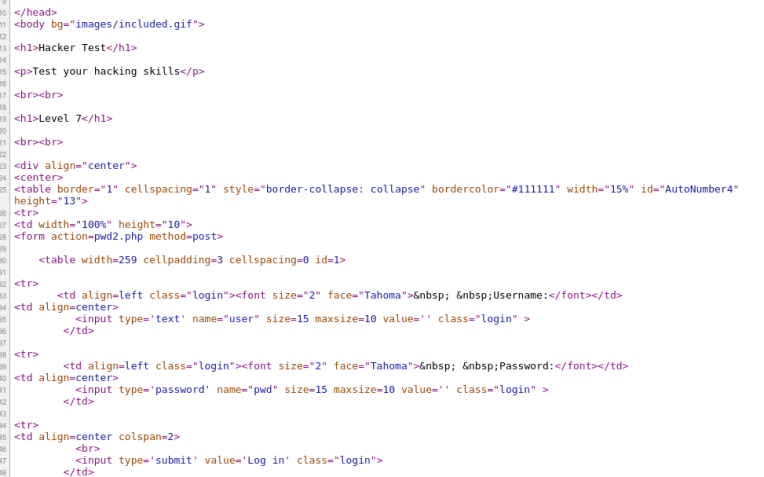
Level 7<!–
var pass;
pass=prompt(“Password:”,””);
if (pass==”hackertestz“) {
window.location=”included.htm”;
}else
alert(“Try again…”);
//–>
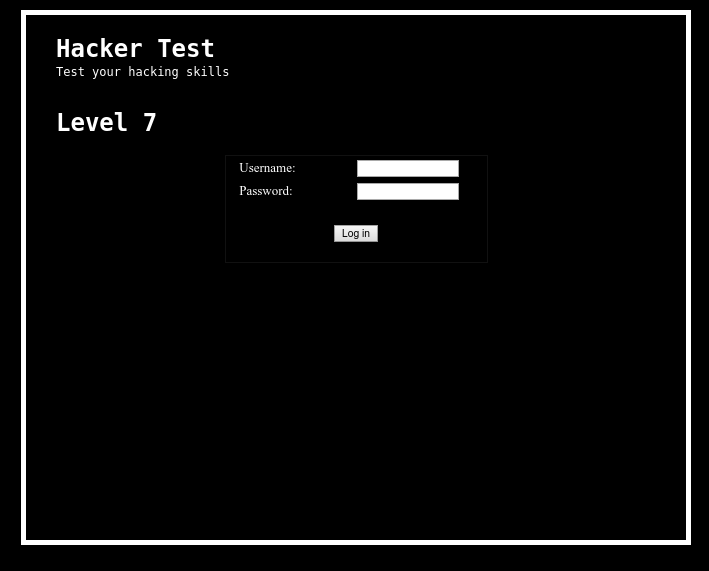
Source:
For challenges like these, be sure to click on and navigate to any links that are included. Navigating to /images/included.gif, the password is written in small font on the lower right hand side of the screen.
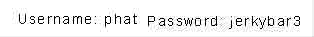

Navigate to phat.php.
Then to ‘images/phat.gif’
We are given another clue written in teeny font on the lower right hand side of the screen. It says ‘look for a PhotoShop Document’ -> PSD. Change phat.php to phat.psd, a file gets downloaded. Open the file with gimp.
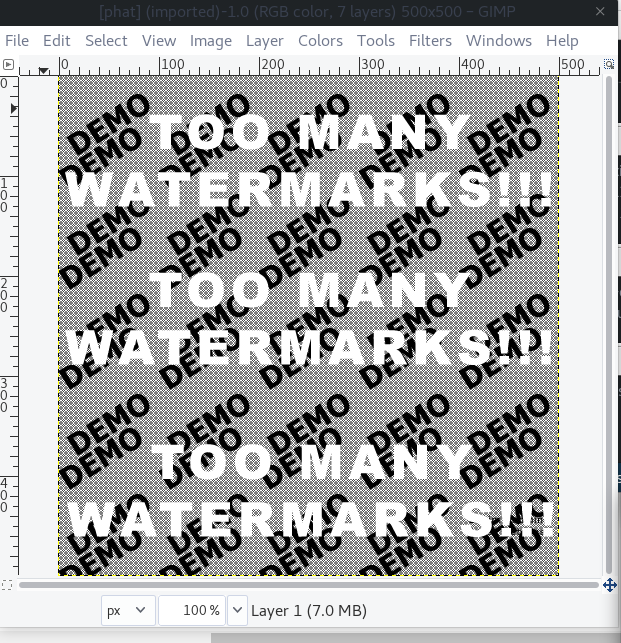
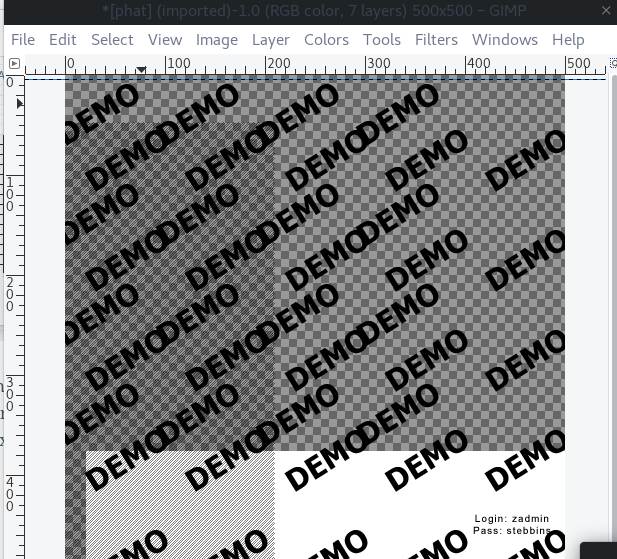
The password is hidden in this picture in the bottom right hand corner of the screen. To view it unobstructed just move the other layers out of the way until the text is fully revealed.
For this level we’re told to ‘crack the password’. When we click to view the source code we’re told ‘no source code is provided for this level’. Instead use ‘inspect’ and expand the code to find the password.

From looking at it I can see it’s been base64 encoded. There are many sites where you can decode the value. Navigate to http://www.hackertest.net/gazebruh.php for level 10.
Level 10
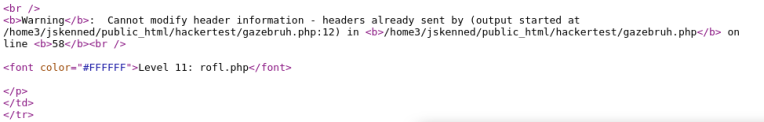
At first look, we can already see something’s up as random letters in the top paragraph are italicized. I bet that’s our password. Now we’re presented with the following error message on the page.
Warning: Cannot modify header information – headers already sent by (output started at /home3/jskenned/public_html/hackertest/gazebruh.php:12) in /home3/jskenned/public_html/hackertest/gazebruh.php on line 58
Append /hackertest/gazebryh.php to the end of the url. Check the source:
Again let’s check the source:

Navigating to ‘images/try.gif’ we get a page that has ‘nice try’ written in teeny letters at the bottom right hand corner. Back to the source, at the top written in the meta robots field content says “goto: clipart.php”
Level 12The page contains the message: “3 letters change everything. Look carefully!” Check the source:

In the meta named ‘clue’ it says “use graphic software”. Click on ‘images/logo/jpg’ and zoom in super close. In large letters written across Europe it says puta.php.
Level 13The meta in the source says same as before ‘use graphic software’. Further down the page gives us the answer.
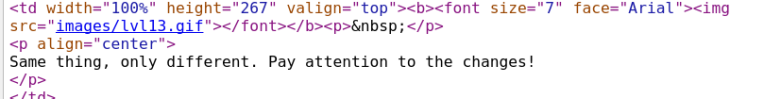
Navigate to the gif and zoom in super close, it says 4xml.php
Level 14Checking the source we’re given the same clue to use graphic software.

Click the bidvertiser.gif link and download the file.

Open the file using gimp.
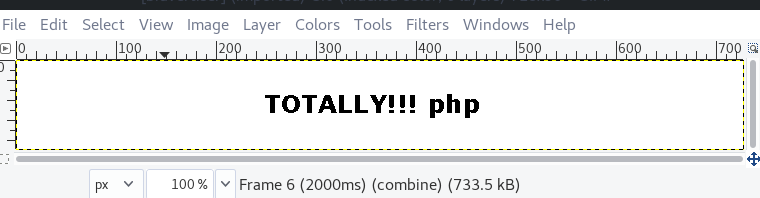
We’re given the following message:
Since you still have your photoshop open, check this out: images/pass2level16.jpg << good luck with it!
Download the file and open with gimp.
-image is unavailable–
hmmmm….I guess try unavailable?
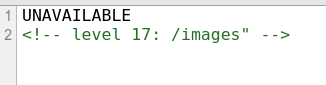
Append ‘/images’ at the end of ‘unavailable’ and check sourecode.
<body background=”bg.jpg“>
Download file and open with text editor. You’ll find Ducky.php. Append that to the url following /unavailable.
Level 16We’re presented with an password input box. Again check the source code. Written about halfway down it says ‘password: your ip address’. To get that open a terminal and type ‘curl icanhazip.com’.
Level 17
Checkout /unavailable/../level18.shtml then check the source. Check out under ‘images’ directory n00b.gif. In the lower right hand corner it says “like a noob!…” Oh, duh..enter n00b as the password.
Level 18Authorization RequiredNavigate to http://www.hackertest.net/level19.shtml Level 19Think like a n00b.
You will need to enable cookies for the Hacker Test Admin Panel to work as expected.
Password:
If you are looking in the script, you are too far, go back.

Download ‘images/n00b.gif and open it with gimp.
Level 20http://hackertest.com/gazebruh2.htm
Advertisements Share this: