Microsoft made a big step forward in the Modern Management field. Limitations like custom configurations or even Win32 App installs can be addressed now. Microsoft developed an EMS agent (aka SideCar) and released it as a new Intune feature called Intune Management Extension. This agent is able to manage and execute PowerShell scripts on Windows 10 devices and it does this quite well.
We can simply upload our own PowerShell scripts for device configuration:
How do we get the agent installed on the devices?
The ability to deploy basic MSI packages via MDM OMA-DM channel, is provided by Microsoft since the beginning of Windows 10. This is achieved by using the EnterpriseDesktopAppManagement CSP.
Microsoft is using this mechanism to deploy the agent to Windows 10 devices. Beginning with Windows 10 Version 1607 we have support of the Intune Management Extension now.
The workflow is basically like this. If a PowerShell script is assigned to a user or device and the agent is not installed, it will be pushed down automatically to the device via EnterpriseDesktopAppManagement CSP by Intune. This can be verified and traced in the “Advanced Diagnostics Report” of the MDM management.
Open Settings > Accounts > Access work or school > Connected to TenantName’s Azure AD > Info > scroll down to the bottom and click “Create report”
 Now you get an report about all MDM configurations including the desktop app installations. Here we can see the EnterpriseDesktopAppManagement msi install of the EMSAgent with the ProductCode: {25212568-E605-43D5-9AA2-7AE8DB2C3D09}
Now you get an report about all MDM configurations including the desktop app installations. Here we can see the EnterpriseDesktopAppManagement msi install of the EMSAgent with the ProductCode: {25212568-E605-43D5-9AA2-7AE8DB2C3D09}

./device/Vendor/MSFT/EnterpriseDesktopAppManagement/MSI/%7B25212568-E605-43D5-9AA2-7AE8DB2C3D09%7D
The instruction can be translated into more human readable form with ProductCode and curly brackets, as the yellow marked resource uses URL encoding and here %7B = { and %7D = }
./device/Vendor/MSFT/EnterpriseDesktopAppManagement/MSI/{25212568-E605-43D5-9AA2-7AE8DB2C3D09}
If the device encounters any error during installation of the agent, we can troubleshoot this with the eventlog:
Start event viewer > Applications and Services Logs > Microsoft > Windows > DeviceManagement-Enterprise-Diagnostics-Provider > Admin
An example where the agent installation went wrong with an error event id 1924 looks like this:
Event ID 1924, Error EnterpriseDesktopAppManagement CSP: An application install has failed. Examine the MSI log (C:\Windows\system32\config\systemprofile\AppData\ Local\mdm\{25212568-E605-43D5-9AA2-7AE8DB2C3D09}.log) for more details. Install command: ("C:\Windows\system32\msiexec.exe" /quiet /l*v C:\Windows\system32\config\systemprofile\AppData\Local\mdm\ {25212568-E605-43D5-9AA2-7AE8DB2C3D09}.log /qn /i "C:\Windows\system32\ config\systemprofile\AppData\Local\mdm\ {BD19E4D8-D6C9-48B2-A53C-579D03B29FE9}.msi" ), MSI ProductCode: {25212568-E605-43D5-9AA2-7AE8DB2C3D09}, User SID: (S-0-0-00-0000000000-0000000000-000000000-000), Result: (User cancelled installation.).Here we can see the original MSI install command including logfile path for further analysis:
C:\Windows\system32\config\systemprofile\AppData\Local\mdm\ {25212568-E605-43D5-9AA2-7AE8DB2C3D09}.log
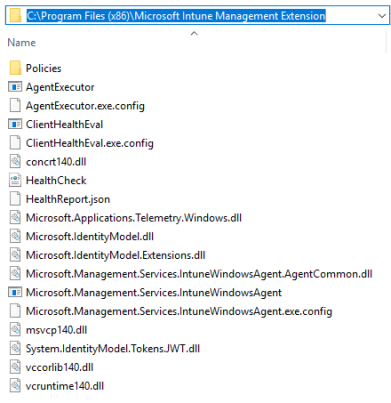
The agent will get installed in the 32-bit Program Files path:
C:\Program Files (x86)\Microsoft Intune Managment Extension
How does the agent gets it’s policy?
The agent will start to figure out the service endpoint via Service Discovery. A common approach in Microservices architecture in modern cloud platforms. After getting the Intune Service URL (https://somemssubdomain.manage.microsoft.com/SideCar/StatelessSideCarGatewayService) the agent can start to communicate and will receive its assigned policies.
All this can be traced in the logfiles here:
C:\ProgramData\Microsoft\IntuneManagementExtension\Logs
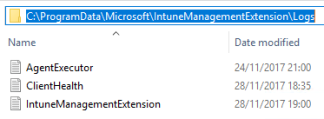
The agent will start to download and execute the assigned PowerShell script here:
C:\Program Files (x86)\Microsoft Intune Managment Extension\Policies\Scripts\UserGUID_ScriptGUID.ps1
and the results are written here:
C:\Program Files (x86)\Microsoft Intune Managment Extension\Policies\Results\UserGUID_ScriptGUID.output|.error|.timeout
After successful execution the script and results are cleaned up and nothing is left on the device. Corresponding registry entries for the assigned scripts and execution results are here:
HKLM\SOFTWARE\Microsoft\IntuneManagementExtension\Policies\UserGUID\ScriptGUID

How often does the agent check for new policies?
The default is every 60 minutes.
What are the PowerShell script execution options?
We can execute scripts in system context or user context. Optional we can enforce a signature check.
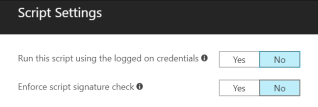
The current file size limit is 10KB for ASCII scripts and 5KB for unicode scripts. The current file size limit is max. 200KB.
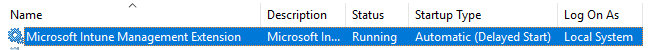
How do I enforce next agent check for policies?
Simply restart the Windows Service “Microsoft Intune Management Extension”.
Is there a particular order in which multiple scripts are executed?
No, they are executed in random order.
What can be done with the PowerShell script execution?
Some examples and potentially pitfalls with the usage of the Intune Management Extension are listed below:
Install Win32 application
Install Win32 applications can be done easily by using a web request to get sources for the installation and finally execution of the sources. This technique is used a lot in the Chocolatey space. A simple example with 7-zip is shown below and can be modified to your needs:
# Author: Oliver Kieselbach # Date: 11/28/2017 # Description: Download executable or msi and execute to install. # The script is provided "AS IS" with no warranties. $url = "http://www.7-zip.org/a/7z1701-x64.msi" $filePath = "c:\windows\temp\7z1701-x64.msi" $ProgressPreference = 0 Invoke-WebRequest $url -OutFile $filePath -UseBasicParsing & $filePath /quietTo use Chocolatey you should follow the install instructions from the Chocolatey website:
iex ((New-Object System.Net.WebClient).DownloadString('https://chocolatey.org/install.ps1'))After Chocolatey Framework installation you can use choco.exe install Package in additional PS scripts to install Chocolatey software. An excellent post from Peter van der Woude regarding Chocolatey and Intune Management Extension can be found here: Combining the powers of the Intune Management Extension and Chocolatey
Write registry keys in x64 hive and not WOW6432Node
As the agent is an 32-bit agent every PowerShell script execution will be in the 32-bit agent process. If we write a registry key on a x64 device from a 32-bit process it will be redirected to the WOW6432Node in the registry. This is often not the desired behavior. To solve this we can restart the script as a 64-bit process for script execution. An example to write a registry key to the x64 hive with this technique is shown below:
# Author: Oliver Kieselbach # Date: 11/28/2017 # Description: Write to registry and ensure execution from x64 process environment. # The script is provided "AS IS" with no warranties. Param([switch]$Is64Bit = $false) Function Restart-As64BitProcess { If ([System.Environment]::Is64BitProcess) { return } $Invocation = $($MyInvocation.PSCommandPath) if ($Invocation -eq $null) { return } $sysNativePath = $psHome.ToLower().Replace("syswow64", "sysnative") Start-Process "$sysNativePath\powershell.exe" -ArgumentList "-ex bypass -file `"$Invocation`" -Is64Bit" -WindowStyle Hidden -Wait } Function New-RegistryKey { Param([Parameter(Mandatory = $true)] [string]$Key, [Parameter(Mandatory = $true)] [string]$Name, [Parameter(Mandatory = $true)] [string]$Value, [ValidateSet("String", "ExpandString", "Binary", "DWord", "Multistring", "QWord", ignorecase=$true)] [string]$Type = "String") try { $subkeys = $Key.split("\") foreach ($subkey in $subkeys) { $currentkey += ($subkey + '\') if (!(Test-Path $currentkey)) { New-Item -Type String -Path $currentkey | Out-Null } } Set-ItemProperty -Path $currentkey -Name $Name -Value $Value -Type $Type -ErrorAction SilentlyContinue } catch [system.exception] { $message = "{0} threw an exception: `n{0}" -f $MyInvocation.MyCommand, $_.Exception.ToString() Write-Host $message } } if (!$Is64Bit) { Restart-As64BitProcess } else { # Enable Potentially Unwanted Application protection New-RegistryKey -Key "hklm:\SOFTWARE\Microsoft\Windows Defender" -Name "PUAProtection" -Value "1" -Type DWord }
Execute in user context and show dialog
To show a simple example to execute scripts in user context we can use the following script to present a Message Box to the user:
Add-Type -AssemblyName PresentationFramework [System.Windows.MessageBox]::Show('Hello World from Sid-Car!')
I hope this explains the technical implementation of the Microsoft Intune Management Extension and the extension addresses some road blockers you might have in the past with Intune regarding advanced configurations.
Share this:




