According to a report conducted by security firm Kaspersky, over 140 financial institutions in 40 countries have been found in the memory of targeted computers. Kaspersky labs alluded to such a type of malware once before 2 years ago in the infamous Stuxnet zero-day attack on Iran and Kaspersky Labs.
According to Threatpost, researchers uncovered “Meterpreter” an advanced, dynamically extensible payload that uses in-memory DLL injection stager found and used in metasploit and maintains its invisibility by residing solely in the memory and using no new processes or disk writing to leave behind file artifacts to be noted by the typical system admin and forensic investigator.
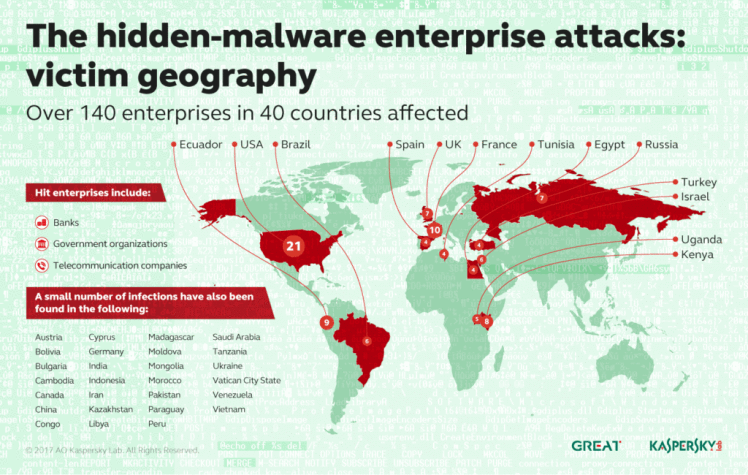 Kaspersky Chart of Meterpreter attacks
Kaspersky Chart of Meterpreter attacks
The goal of this malware was to stealthily siphon passwords of system administrators and exploit malicious powershell scripts via Microsoft’s NETSH, to funnel traffic from the victim’s host to the attacker’s command and control system. How attackers got initial access is still up to discussion with Ars Technica suggesting an employee being hit by a SQL-injection and Threatpost claiming an undiscovered zero-day in conjuncture with other metsaploit tool Mimikatz. The big picture remains that such attacks have been known to compromise over 1 Billion USD via the usage of Meterpreter and pivoting between internal systems to funnel money out of client accounts to attacking groups and individuals.
Moving forward, Meterpreter announces the stakes in Digital Forensics towards memory forensic analysis and the failing compromise of anti-malware and anti-virus towards the detection of such attacks as purporters of these exploits are aware of their capability of being stifled by trained forensic investigators; particularly when they’re able to siphon he data using the legitimate applications held on the system. Kaspersky itself however seems to be cautiously optimistic citing
“We’re looking at the common denominator across all of these incidents, which happens to be this odd use in embedding PowerShell into the registry in order to download Meterpreter and then carry out actions from there with native Windows utilities and system administrative tools.”
Nevertheless, with the recent rise of hotels, restaurants, and franchise chains being compromised the need to detect exploits such as these will only become more important for all businesses and their cybersecurity strategies.
Resource Links:
https://threatpost.com/fileless-memory-based-malware-plagues-140-banks-enterprises/123652/
https://arstechnica.com/security/2015/06/stepson-of-stuxnet-stalked-kaspersky-for-months-tapped-iran-nuke-talks/
Advertisements Share this:




